On April 16th 2025, Solana quietly patched a zero-day vulnerability in its Confidential Transfers feature — powered by zero-knowledge proofs (ZKPs). The bug could’ve let attackers mint unlimited tokens. And here’s the real problem: no one really knows if bugs like this in ZKP systems have actually been exploited. There’s no audit trail. No accountability. Not for the issuer. Not for regulators. Not for users. Just a silent, irreversible break in the integrity of the ledger.
This is the catch with ZKPs used for general purpose, scalable privacy: when they fail, they fail invisibly. You don’t get a second chance. And you don’t get a clean fix. In regulated finance, where every record needs to be verifiable and every risk must be traceable, that’s not just a technical issue — it’s a dealbreaker.
Yes, ZKPs are a powerful cryptographic tool. And they’ve earned a place in scaling systems like zk-Rollups. But let’s be clear: they are limited when it comes to carrying the weight of institutional trust due to ongoing challenges in security and performance. The privacy techniques you choose must be fit for purpose. ZKPs are essential in systems like ZCash that prioritize ideals like censorship resistance, and where users are willing to accept certain trade-offs to achieve it. But when used as the foundation for privacy at scale in regulated financial markets, opacity is a liability. Privacy without proof isn’t privacy — it’s a risk waiting to surface.
Understanding zk-Rollups: Scalability Over Privacy
zk-Rollups are a popular application of ZKPs in blockchain, primarily used to enhance scalability rather than privacy. Examples are StarkNet, zkSync, Polygon zkEVM to name just a few. In zk-Rollups, transactions are processed in a batch or "rollup" and then translated into a single proof, with a new state root hash. This proof, along with the state root hashes and transaction call data, are published on the main chain (e.g. Ethereum). The computation and storage of the state are off-loaded to a secondary layer (L2), allowing for increased transaction throughput by reducing the data that needs to be processed directly by the main chain. However, it is crucial to note that this does not enhance privacy: transaction data is visible on the L1 chain, and all participants in the L2 can see the entire state and transaction details.
Privacy Pools and Anonymity
Another application of ZKPs in blockchain is in privacy pools, such as those used in ZCash or Tornado Cash. Users can deposit tokens into a pool where they are mixed with the same type of asset of many other users. During withdrawals, a ZKP is used to prove that the user made a deposit and that that deposit has not yet been withdrawn, while crucially not revealing which specific deposit is being withdrawn. This breaks the on-chain link between source and destination addresses. This application does provide a form of privacy - specifically enhanced pseudonymization - but requires careful handling to avoid other methods of tracking and linking transactions, such as network analysis or correlating user behavior patterns. Past challenges like those leading to the sanctioning of Tornado Cash may be overcome in the future. But it is important to note that these techniques only provide anonymous/pseudonymous token holding and transfers through mixing with many other users, not general confidentiality for smart contracts.
From Battleships to Balance Sheets: ZKPs Aren’t Ready But Canton Is
There is a fair amount of research to use ZKP to maintain private state on general purpose smart contracts. These are contracts where the state (information about balances, game states, etc.) is kept hidden from all parties except those explicitly authorized. The ZKP is used here to confirm that operations on this hidden data are executed correctly, without revealing the data itself. Typical use case examples that are shown are:
- Battleship - Each side of the board is private to one of the players. The problem ZKPs solve here is that when player A “shoots” a field on player B’s board, and B reports a hit or miss, A can ascertain that B is telling the truth without learning anything more about B’s side of the board.
- Tokens - The mapping from account to quantity is private. During a transfer, the user uses a ZKP to prove that the quantities on inputs and outputs match without revealing any of the quantities.
Promising Yet Early-Stage
Projects that explore such general ZKP privacy include Midnight, Aztec, Aleo, and Zokrates.
All projects in this space are still in the developmental phase. Toy examples like the above demonstrate the potential of ZKPs but also highlight the challenges of implementing such complex cryptographic tools in practical, real-world scenarios. I discussed these in more depth in the blog “Some Hard Truths About Blockchain”. One of the scariest in my view is the non-auditability of bug exploits.
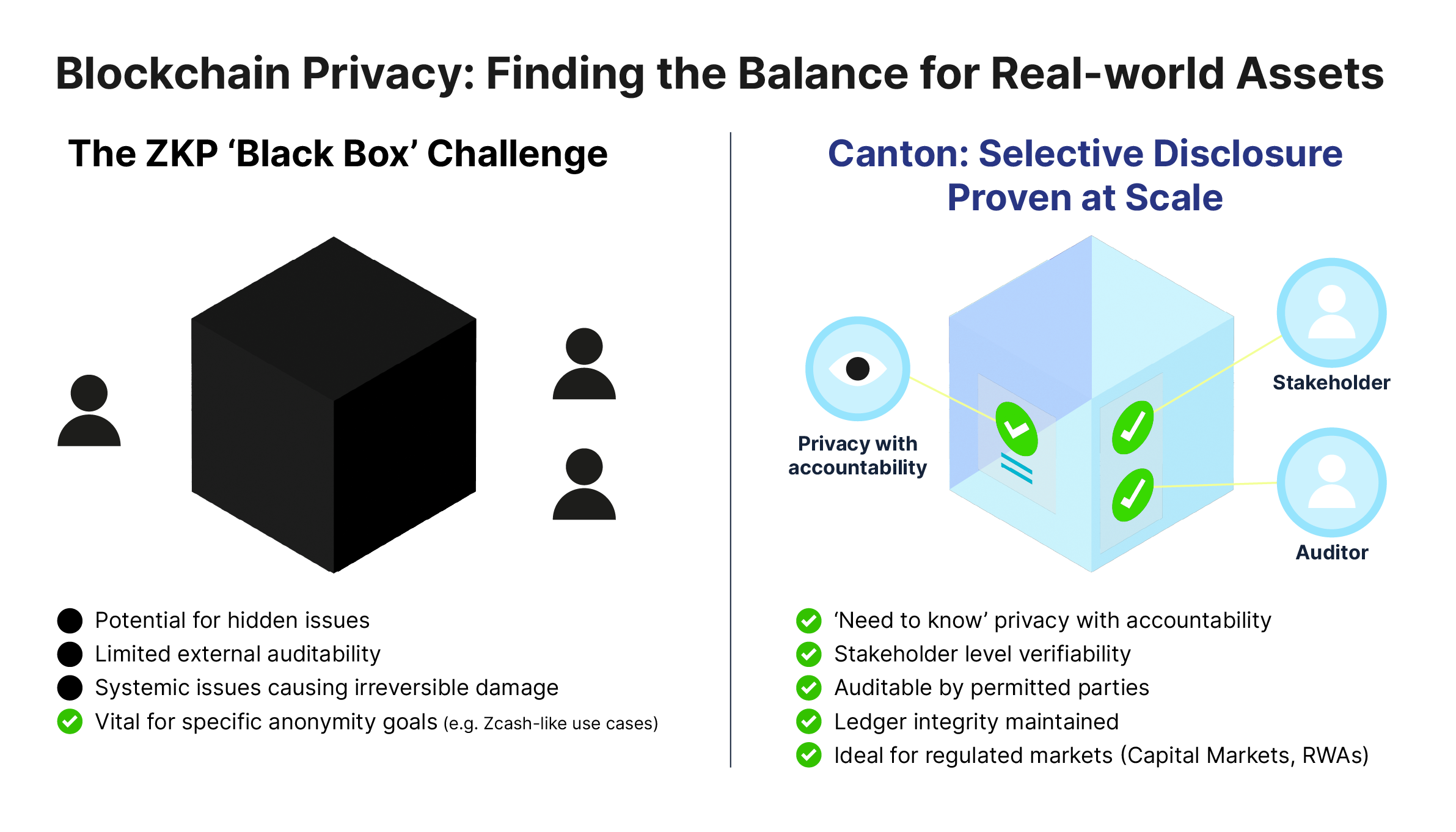
Organizations relying on ZKPs for general-purpose privacy will always face one unavoidable truth: they cannot confidently tell users or regulators whether their systems have been compromised. A single undetected exploit can permanently taint the ledger, and no off-chain workaround can restore trust or transparency. If your fallback is keeping separate records, then you've abandoned the very principle of blockchain.
You don’t have to wait for general-purpose privacy to become real — it already is. Canton delivers smart contract privacy with full auditability, and it's live today at scale. That’s why banks like Goldman Sachs and HSBC are building on it, and why it's powering on-chain collateral transformation with institutions like Euroclear and market makers, including QCP and Flowdesk. This isn’t theoretical. It’s production-grade, regulator-ready privacy — engineered for what’s real.
Why Wait? Real Privacy is Already Here
Zero-knowledge proofs have real potential — especially in scaling and narrow privacy use cases like token mixers. But when it comes to general-purpose privacy for smart contracts, they’re still experimental. They don’t protect organizations from silent failures or provide the auditability to prove everything is ok. The use of ZKPs in contexts like zk-Rollups does not inherently protect transaction details from being public. For institutions that need confidence, auditability, and control, these are threshold issues.
These are high-stakes systems. Trust can’t be based on hope.
That’s why leading firms aren’t waiting. The Canton Network is already delivering real, highly programmable privacy at scale — with auditability, recoverability, and system integrity. It’s live, it’s proven, and it’s built for the realities of financial markets on-chain.